Key Points:
- Numerous of websites targeting Android and Windows users have been discovered to provide trojanized versions of WhatsApp and Telegram applications.
- The majority of these applications make use of clipper malware, which is intended to steal or change the contents of the Android clipboard.
- The trojanized applications mostly targeted Chinese users.
According to ESET Research, a network security research company, criminals were discovered employing counterfeit versions of Telegram and WhatsApp programs with malware in an effort to steal cryptocurrency.

Clippers are a sort of malware that may steal or manipulate the contents of the clipboard, according to reports. This is the first time ESET Research has seen Android clippers explicitly targeting instant messaging. According to the languages utilized by these counterfeit apps, the operators behind them seem to be primarily targeting Chinese users.
This software may change the bitcoin wallet addresses that victims provide in chat messages to those of the attackers. Some clippers employ optical character recognition to steal bitcoin wallet recovery phrases and extract information from images. ESET discovered remote access Trojans with malicious Windows versions of WhatsApp and Telegram, in addition to cutters.
Although the first incident of clipper malware on the Google Play Store was in 2019, this is the first time that Android-based clipper malware has been integrated into instant messaging applications.
Moreover, some of these applications employ optical character recognition (OCR) to detect text from screenshots saved on hijacked devices, which is Android malware first.
The assault chain starts with naïve consumers clicking on false adverts in Google search results, which redirects them to hundreds of shady YouTube channels, which then redirects them to spoof Telegram and WhatsApp websites.
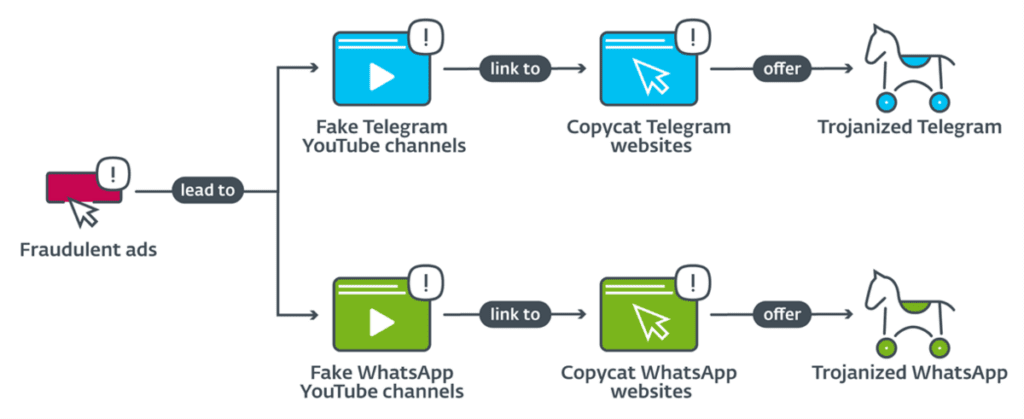
ESET Research also discovered Windows versions of the wallet-switching clippers, as well as Telegram and WhatsApp Windows installers laced with remote access trojans (RATs). As a break from tradition, one of the Windows-related malware bundles is made up of RATs rather than clippers, allowing complete control of the victim’s PC. This allows RATs to steal bitcoin wallets without interfering with the application flow.
“Install apps only from trustworthy and reliable sources, such as the Google Play store, and do not store unencrypted pictures or screenshots containing sensitive information on your device. If you believe you have a trojanized version of Telegram or WhatsApp, manually remove it from your device and download the app either from Google Play or directly from the legitimate website,” recommends ESET researcher Lukáš Štefanko, who found the trojanized applications.

Malware is becoming more sophisticated in its ability to trick consumers, and it may appear anywhere. As Coincu reported, a Twitter user claimed to have unwittingly downloaded malware detected via a Google Adwords search result, losing their whole net worth in nonfungible tokens and cryptocurrencies.
DISCLAIMER: The Information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing.
Join us to keep track of news: https://linktr.ee/coincu
Harold
Coincu News