Lazarus Group Bounty Website Now Launched By Bybit to Recover Stolen Funds
Key Points:
- Bybit has introduced a bounty website to track Lazarus Group’s money laundering activities, offering a 10% reward for recovered funds.
- The North Korea-backed group is suspected of stealing $1.4 billion from Bybit in a February 21 Ethereum exploit, following similar attacks on other exchanges.

Bybit has launched a dedicated bounty website aimed at tracking the money laundering activities of North Korea’s Lazarus Group.
The initiative, announced by Bybit CEO Ben Zhou, is designed to enhance transparency in tracing stolen cryptocurrency and recovering funds after the Bybit hack, which is believed to be the largest breach in crypto industry history.
Bybit Launches Bounty to Track Lazarus Group’s Laundering
The exchange previously pledged a bounty totaling 10% of any recovered assets, potentially reaching as high as $140 million.
The reward will be split equally, with 5% allocated to entities that successfully freeze stolen funds and the other 5% awarded to contributors who assist in tracking the illicit transactions.
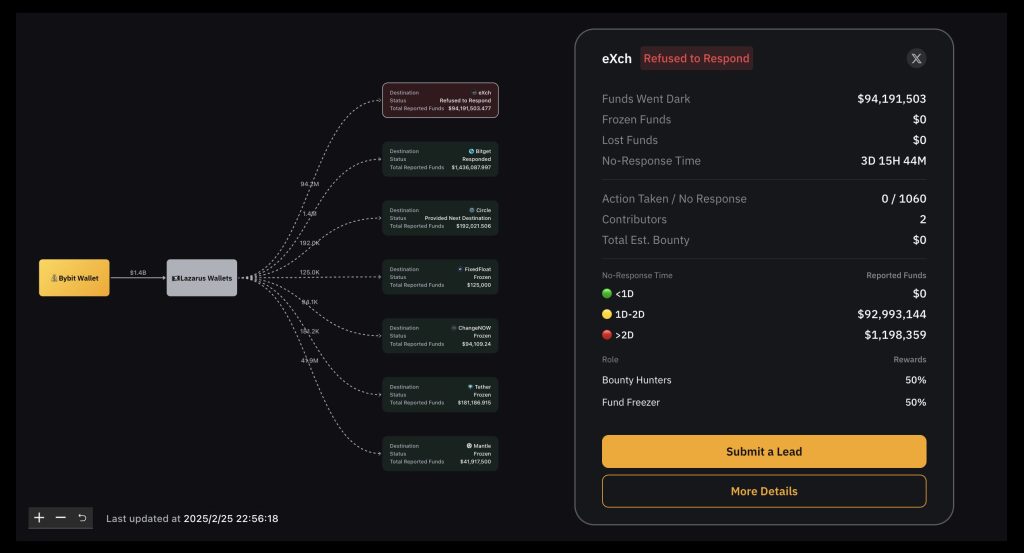
The effort comes in response to what has been described as the largest cryptocurrency heist to date. On February 21, the Dubai-based exchange fell victim to an Ethereum exploit, with Lazarus Group suspected of orchestrating the attack. The breach resulted in a staggering $1.4 billion loss, marking a significant blow to the digital asset industry.
How Lazarus Launders Stolen Cryptocurrency
Blockchain investigator ZachXBT was among the first to link the incident to Lazarus Group, a finding later corroborated by crypto intelligence firm Arkham Intelligence.
ZachXBT also revealed that Lazarus was behind a similar attack in January against Singapore-based exchange Phemex, where hackers stole over $69 million.
Blockchain analytics firm Elliptic detailed the money laundering techniques employed by Lazarus. The group follows a structured two-stage process to obscure the origins of stolen funds. Initially, hackers convert pilfered tokens into native blockchain assets like Ether to evade issuer-imposed freezes.
Subsequently, they distribute the funds across multiple wallets in a tactic known as “layering,” complicating efforts to trace and recover the stolen assets. Within two hours of the Bybit breach, the hackers had dispersed the funds across 50 different wallets, each containing approximately 10,000 ETH.
Lazarus Group has a long history of cybercrime, with ties to North Korea’s state-sponsored hacking operations. The group first gained notoriety in 2009 and made global headlines in 2016 after stealing $81 million from Bangladesh Bank. A year later, it was behind the devastating WannaCry ransomware attack, which infected over 300,000 computers across 150 countries.
| DISCLAIMER: The information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing. |























