Key Points
- THORChain and Bybit hack are at the center of a major crypto laundering case, with over $240M in stolen funds funneled through THORChain.
- Investigations reveal North Korea’s Lazarus Group exploited THORChain’s cross-chain swaps to move stolen ETH to Bitcoin.
- The controversy has led to internal division within THORChain, with key developers resigning amid backlash.
- The THORChain community debates whether to implement stricter security measures or maintain decentralization.

Arkham Intelligence reports that hackers laundered $240M from the Bybit hack via THORChain, using its cross-chain swaps to evade detection.
On-chain analytics from Arkham and Dune reveal that 93% of ETH deposits on THORChain since February 21 originated from hacker-linked wallets. This data, combined with previous cases, suggests Lazarus Group utilized the platform to convert stolen ETH into Bitcoin.
Lazarus Group exploits THORChain after Bybit hack
On February 28, on-chain analytics firm Arkham Intelligence reported that at least $240 million from the Bybit hack had been funneled through THORChain, a decentralized exchange (DEX) known for facilitating cross-chain swaps without intermediaries. Most of these stolen funds were converted from ETH to BTC, allowing the hackers to further obscure their tracks.
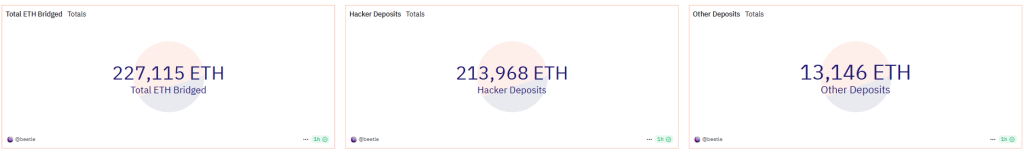
Blockchain sleuths, including beetle (@1kbeetlejuice), quickly assembled dashboards on Dune Analytics to track illicit flows. Their findings were alarming: 93% of ETH deposits on THORChain since February 21 originated from hacker wallets, making Lazarus Group the dominant liquidity provider on the platform.
By the time of reporting, over 227,115 ETH (~$490.5M) had been processed through THORChain, raising concerns that the protocol had become a primary tool for money laundering in the Bybit hack.
eXch restricts swaps, forcing hackers to rely on THORChain
Before moving the stolen ETH to THORChain, the hackers utilized multiple tools to break transaction trails. On-chain data reveals they employed Asgardex, DeFiSwap, FortunaSwap, GemWallet, LiFi, ShapeShift, TrustWallet, and other DeFi protocols to fragment and conceal their movements.
Meanwhile, eXch, another non-custodial bridge used by the hackers, suddenly disabled ETH and ERC-20 swaps, effectively blocking $94.2 million from being laundered. This forced the attackers to shift their laundering strategy, increasing their reliance on THORChain for cross-chain transactions.
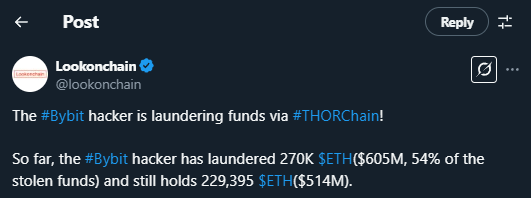
As of February 28, Lazarus Group had laundered 270,000 ETH (~$600M) through THORChain, representing 54% of the total stolen funds.
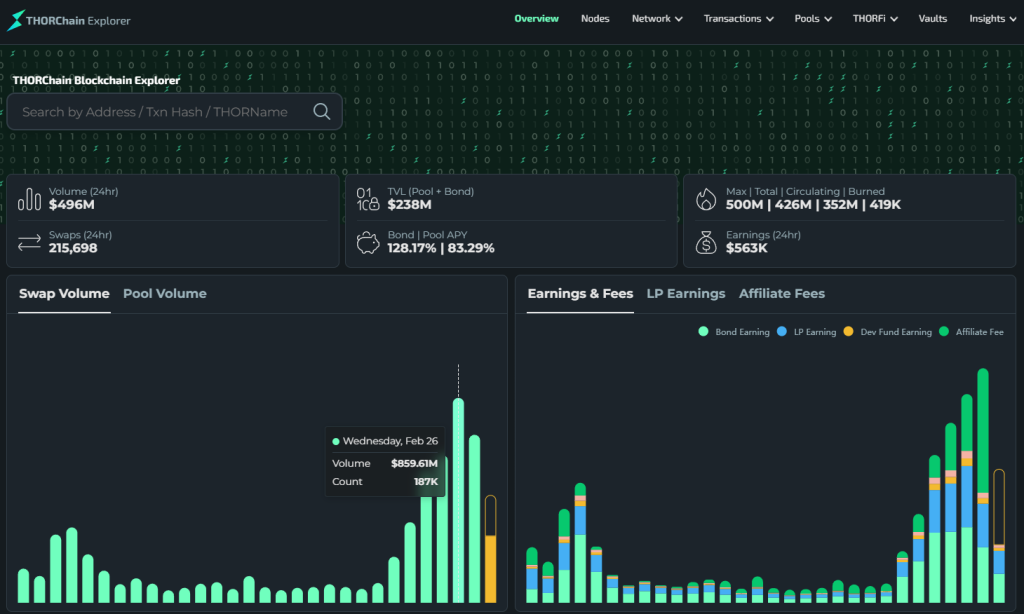
The sheer volume of transactions caused THORChain’s daily trading volume to skyrocket to $859,61 million on February 27, the highest in its history.
Internal turmoil: Developers resign over lack of action
The influx of illicit funds sparked heated debates within the THORChain community. Paradigm researcher samczsun pointed out three major reasons why THORChain was an attractive option for hackers:
- Direct access to Bitcoin: THORChain’s unique feature of allowing native BTC swaps made it ideal for Lazarus Group, which typically cashes out through BTC before converting to fiat.
- Reliance on THORChain by eXch: eXch depended on THORChain to source BTC for its swaps, inadvertently facilitating the laundering process.
- Validator governance loopholes: Attempts to block suspicious transactions were overturned within minutes due to THORChain’s decentralized validator model.
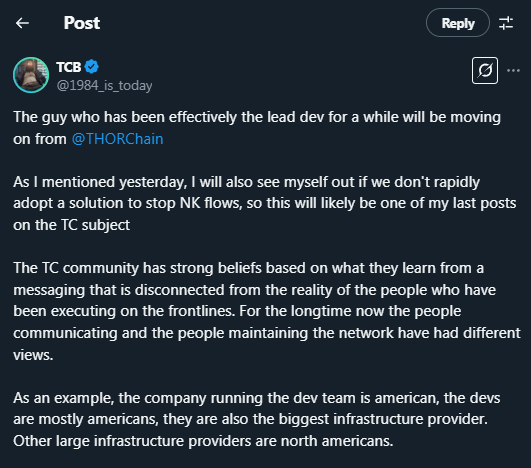
Amid the growing backlash, THORChain’s core developer Pluto resigned, citing frustration over the protocol’s inability to address illicit activity.
Similarly, TCB, one of the three validators who voted to halt ETH trading on THORChain, also announced their departure, warning that Lazarus Group’s dominance over THORChain liquidity posed a national security threat.
What’s next for THORChain amid the Bybit hack fallout?
Despite mounting pressure, THORChain’s founder John-Paul Thorbjornsen defended the platform’s stance, arguing that none of the flagged hacker addresses were officially listed by the OFAC or FBI. He opposed any third-party blacklist being integrated into the protocol, stating that THORChain does not launder money and that it was up to centralized exchanges to track and freeze stolen funds.
However, the crisis has already taken a toll on THORChain’s RUNE token, which dropped 11% within 24 hours, trading at around $1.31.
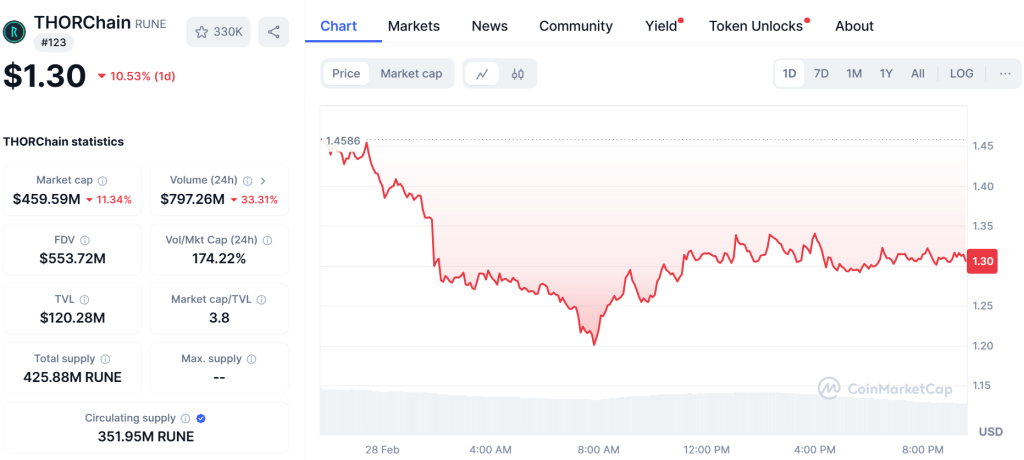
With over $1.5 billion stolen in the Bybit hack, the continued exploitation of THORChain raises serious questions about the role of decentralized platforms in financial crimes. Whether THORChain will take action or maintain its “purely decentralized” philosophy remains to be seen.
| DISCLAIMER: The information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing. |





















