Ethereum “Vanity Addresses” Made Using The Profanity Tool, Hackers Stole $3.3 Million
According to on-chain data from Etherscan, a hacker stole $3.3 million from several Ethereum addresses created with a program called Profanity.
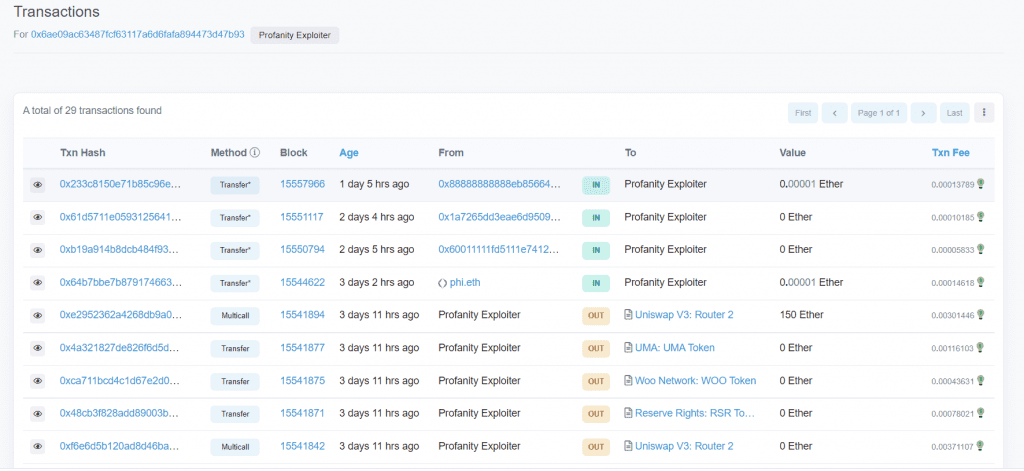
The exploit was first identified by anonymous security analyst ZachXBT on September 16.
Vanity addresses are a form of personalized wallet that include recognizable names or numbers. In the crypto industry, they are largely used as a form of display, similar to how vehicle owners spend exorbitant prices for fancy license plates.
These addresses can be produced using a variety of tools – Ethereum

According to a security disclosure report issued last week by decentralized exchange aggregator 1inch, “vanity addresses” created with Profanity were not secure. The private keys associated with addresses produced through profanity could be retrieved using brute force calculations every 1inch.
However, the security flaw that 1inch brought up could not be resolved in time to stop an exploit. According to Profanity’s unknown developer, “johguse,” development on the game ended a few years ago.
Before 1inch’s revelation, johguse had identified the tool’s vulnerability and forbade users from using it. Following the 1inch discovery, on-chain sleuth ZachXBT claimed last Friday that an unknown hacker had allegedly used the same weakness to steal an estimated $3.3 million in cryptocurrency from a number of profanity-based addresses. The stolen money was transferred from the victims’ accounts to a new Ethereum address that is thought to be under the hacker’s control.
The $3.3 million exploit has drawn comments from experts who suspect that malicious hackers may have known about the security issue in advance.
“Seems like the attackers were sitting on this vulnerability, trying to find as many private keys as possible of vulnerable Profanity-generated vanity addresses before the vulnerability gets known. Once publicly exposed by 1inch, the attackers cashed out in a few minutes from multiple vanity addresses,” Tal Be’ery, security lead and chief technology officer at ZenGo, said.
Notably, 1inch also noted in its study that hackers had previously leveraged the vulnerability for potential attacks with a potential value of millions of dollars. 1inch said that in order to reach its conclusion, it was able to use GPU chips to recompute portions of the private keys for Profanity’s vanity addresses.
DISCLAIMER: The Information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing.
Join CoinCu Telegram to keep track of news: https://t.me/coincunews
Follow CoinCu Youtube Channel | Follow CoinCu Facebook page
Annie
CoinCu News























