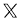$103455.192
At CoinCu News, we give both basic and in-depth articles on the latest news in the cryptocurrency and blockchain sectors.
Mayowa is a seasoned freelance writer specializing in creating compelling, high-converting content across diverse industries.
With extensive experience working with major news outlets, personal blogs, and private clients, he brings a deep understanding of audience engagement and storytelling. His expertise spans SEO optimization, persuasive copywriting, and niche versatility, ensuring content that resonates and delivers results.
Armed with a strong command of the English language and a keen eye for detail, he crafts content that is both impactful and strategically tailored to meet client goals.
News
Prosecutors Accused of Withholding Evidence in Crypto Case
Defense alleges withheld evidence in key crypto legal battle over non-custodial operations.
May
BSC Foundation Allocates $25,000 to WOD, KILO, KOMA Tokens
BSC Foundation invests $25,000 in WOD, KILO, and KOMA tokens, continuing strategic purchases within the
May
Heritage Distilling Adopts Crypto for Payments and Reserves
Heritage Distilling implements cryptocurrency strategy, allowing Bitcoin and Dogecoin for payments and reserves, targeting the
May
Binance CEO Shares Security Tips to Counter Phishing Threat
Binance's CZ reveals anti-phishing tactics to bolster crypto security amidst rising cyber threats.
May
Binance and Kraken Defend Against Social Engineering Attacks
Binance and Kraken repel social engineering attacks, protecting user data and assets successfully.
May
Trump Family’s Crypto Project Faces 15% Portfolio Loss
The Trump affiliated WLFI crypto project records a 15% decline, equating to a $53.07M unrealized
May
France Enhances Security for Crypto Entrepreneurs Amid Kidnappings
France ramps up security for crypto entrepreneurs following a surge in kidnappings. Key measures include
May
Trump Family’s Crypto Stablecoin Responds to Senate Investigation Inquiry
World Liberty Financial's USD1 stablecoin, linked to Trump, faces a Senate probe on regulatory connections,
May
Argentine President Milei Faces Probe Over LIBRA Cryptocurrency
Argentina's Central Bank lifts secrecy on President Milei's transactions in LIBRA scandal. Assets frozen pending
May
[tptn_list how_old="7" limit="5" title_length="0" heading="0" show_date="0" ]
[tptn_list how_old="30" limit="5" title_length="0" heading="0" show_date="0" ]