Key Points:
- Here are 11 popular anti-phishing attack plugins.
- Phishing attacks on the blockchain industry are mainly distributed in two points: domain names and signatures – fake domain names.
On January 28, Azuki’s Twitter account was hacked, causing his fans to connect to phishing links, over 122 NFTs were stolen, and the loss exceeded $780,000. On January 26, the wallet of Kevin Rose, the founder of the NFT project Moonbirds, was stolen. About 40 NFTs were stolen, and the loss exceeded US$2 million. Assets licensed by OpenSea. On January 15th, @NFT_GOD clicked on a phishing ad link on Google, resulting in the theft of all accounts (substack twitter, etc.), cryptocurrencies, and NFTs.
Why are ordinary users and project founders repeatedly attacked by phishing attacks? What anti-phishing browser plug-ins are there on the market? This article makes an inventory of 11 anti-phishing attack plugins.

Mainstream plugins (over 10,000 installs)
- PeckShieldAlert: 50k+ installation times, Chinese and English interface. PeckShield team product.
The website shows that the number of malicious addresses included is 1,286,478, and the number of phishing websites included is 90,931, and it is constantly being updated. Currently only two chains, ETH and BSC, are supported.
Included functions: Token contract monitoring, wallet authorization management, active defense against fraudulent token threats, active defense against phishing website threats, trusted domain name detection, malicious plug-in detection and other anti-phishing website functions.

- Pocket Universe: 20k+ installations, available for Firefox, Microsoft Edge, Google Chrome and other browsers, only applicable to the ETH mainnet. Claims to have cooperation with Metamask and Coinbase wallets.
Included features: detection of malicious Seaport transactions, Honeypot NFTs, and phishing sites.
Use features: do not link the wallet, verify the transaction security by simulating the transaction, slightly affect the transaction speed (no more than 1 second).
- Revoke.cash: 10k+ installations, Chinese and English interface. Works with all EVM-based chains like Ethereum, Polygon, and Avalanche, available in browsers like Firefox, Microsoft Edge, Google Chrome, etc.
Included features: warnings will pop up for transactions on non-whitelisted NFT trading websites and phishing websites; authorization can be revoked.

- Fire: 10k+ installations, suitable for Ethereum mainnet and Polygon. Compatible with MetaMask and Coinbase wallets, works with any Ethereum wallet.
How it works: Monitors the security of scanned transactions by simulating the ERC-20, ERC-721, and ERC-1155 transactions affected by users.
Niche plugins (less than 10,000 installs)
- Wallet Guard: 6k+ installations, incubated by Binance Labs.
Features: Block access to recently created and low-trust websites, automatically disable malicious extensions, monitor and block access to phishing websites.
- MetaDock: The number of installations is 3k+, the code is open source, and the product of the security company BlockSec team.
Function: Only supports BTC, ETH, BSC, Polygon, Fantom, Arbitrum, Cronos, Avalanche, Optimism, Moonbeam public chains and Opensea. You can view the flow of funds in the address, monitor the risk of NFT collections, and interact with products such as Debank and NFTGo.
- Blockem: 930 installations
Function: AI algorithm simulation transaction and address scoring

- Metashield: The number of installations is 864, the code is open source, and the first project incubated by BuidlerDAO.
Working principle: identify approve and send transactions, and use black and white lists and check the status of authorized addresses to help users warn and block phishing websites. No need to connect wallet, no authorization required.
- Stelo: 628 installs, open source code, suitable for any Chromium-based browser.
How it works: Stelo suspends transaction requests sent to Metamask by wrapping the window.ethereum Javascript object that Metamask injects into the page. Once the user approves the transaction in Stelo, it resumes the Metamask request, and if the user rejects it, it cancels the request.
- Scam Sniffer: The number of installations is 615. The code is open source.
Included functions: Detector API (monitoring malicious behaviors such as transferring user assets and requesting authorization), simulated transactions, etc.
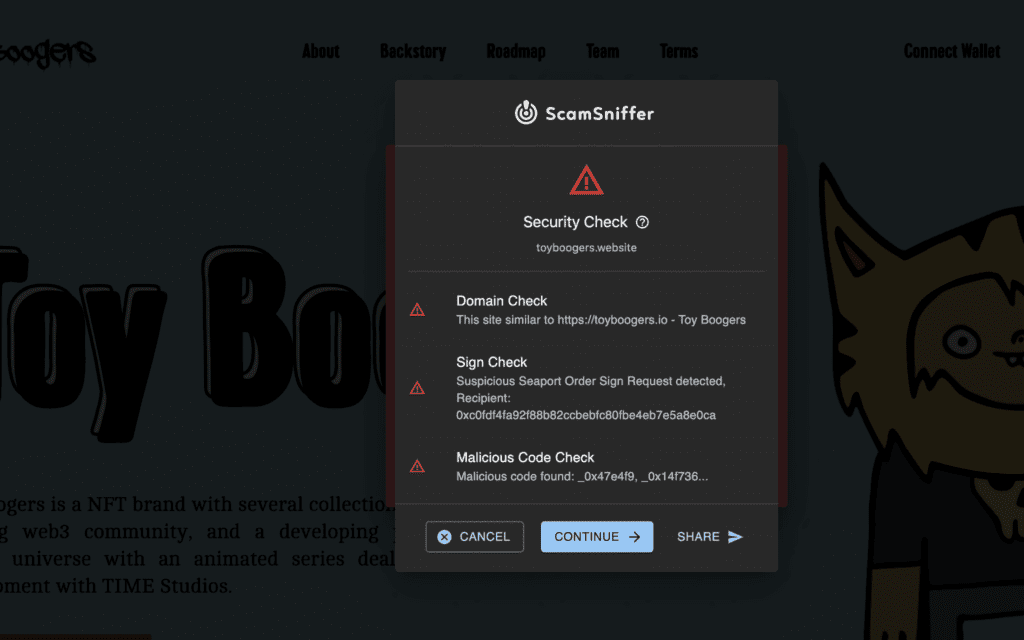
- Beosin Alert: 291 installations, developed by the team of Beosin, a blockchain security audit company.
Inventory summary
Cosine, the founder of SlowMist, said that he has focused on Scam Sniffer, Revoke.cash, Wallet Guard, Pocket Universe, and Fire.
The most used and full-featured is PeckShieldAlert. But in terms of the number of installations, it is almost negligible compared with MetaMask 10M+ and Phantom 2M+. In addition, there is no financing information in this field, which shows that no real attention has been paid to it from the perspective of users or investors.
SlowMist team member @IM_23pds opinion:
Phishing attacks on the blockchain industry are mainly distributed in two points: domain names and signatures, and 90% of NFT phishing attacks are related to fake domain names. If the user opens a phishing page, the relevant plug-ins and browsers can directly prompt the risk, so that there is no subsequent step of fraudulent signature, and the risk can be blocked in the first step.
The 360 era in the previous Web2 world solved the problem of virus attacks for novice users at that time, but it did not solve the problem of Trojan horse viruses. There is always a time difference between virus detection and virus prevention (a professional technology to avoid anti-virus software detection and killing, you can Google it yourself). How to make the time difference smaller, the number of samples faster, and the identification more accurate determines the anti-virus software degree of power.
Similarly, in the blockchain and NFT industries, how to identify and remind the real-time situation of phishing sites in the first step, and the feedback speed and recognition degree on the user end also determine the ability of an anti-phishing plug-in; Identifying these phishing domain names in the first step will greatly increase the risk of users losing coins.
Previously, if the wallet had fraudulent signature identification, it could well display the detailed information of the user’s signature, such as what to authorize, how much, to whom, and other human-readable data, and it could also avoid theft to a certain extent. However, although MetaMask currently has a market share of 80%, the analysis is really difficult.
Although there are some products that do a good job in analysis, they still cannot prevent the loss of coins and NFT. Any products, articles, and reminders are auxiliary. Only by establishing your own security awareness can you be able to stand on a place where you don’t lose coins or NFTs. Personal safety awareness is king.
Blockchain researcher @tmel0211 opinion:
The technical logic of self-custodial wallets such as MetaMask is to help users safely keep local private keys, process user transaction signatures, provide gateways to connect to the main networks of major blockchains, and facilitate smart contract interactions such as DeFi.
In theory, it is feasible to embed any plug-in service that optimizes the experience without affecting the wallet transfer interaction function. Anti-phishing address screening can only be regarded as one of the rigid requirements.
However, the functions of the current mainstream wallet products are very simple, and they are very restrained in service optimization. The reasons are as follows:
- Affected by the client information payload, mobile terminal interaction needs to be more concise than browser plug-ins;
- Affected by decentralized consensus, phishing websites, blacklist libraries, etc. need centralized operation and maintenance support, which will generate consensus
- Affected by the tendency of commercialization, although the service mezzanine can optimize the experience, it is difficult to commercialize it.
At present, mainstream browser security plug-ins in the market are mostly provided by third-party security data companies: the experience is good, but the popularity is not enough. They all have a dream to become 360 security guards guarding web3, although the road is long and difficult:
- The plug-in that provides plug-in services also has potential security risks, and its trust consensus needs time to accumulate;
- Active users who often trade in the DEX environment or Mint NFT currently have weak security awareness, and user habits need to be developed;
- The operation and maintenance challenges of phishing website update and blacklist address database are great;
In our opinion, the wallet narrative should tend to be vertically segmented.
- Minimalist wallet for geeks;
- Safe interactive anti-phishing wallet for beginners;
- Customizable wallet for institutions;
- MPC wallet;
- Smart contract wallet, etc.
But in any case, this does not conflict with the security plugin service market. At this stage, they coexist and complement each other. We believe that an excellent browser security plug-in will eventually become a standard configuration like a wallet.
DISCLAIMER: The Information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing.
Join us to keep track of news: https://linktr.ee/coincu
Harold
Coincu News























