| Key Points: – The 1inch vulnerability in the outdated Fusion v1 parser smart contract led to losses exceeding $5 million. – 1inch is working with affected resolvers, urging contract audits and updates, while launching a bug bounty program offering up to $500,000 in rewards. |
On March 5, blockchain security firm SlowMist identified suspicious transactions linked to 1inch, a decentralized exchange aggregator, with estimated losses of approximately $5 million.
The 1inch vulnerability was traced to a violation in its outdated Fusion v1 parser smart contract.
1inch Vulnerability Emerges Due to Smart Contract Exploit
According to SlowMist’s analysis, the exploit led to losses of around 2.4 million USDC and 1,276 WETH, surpassing $5 million in total. Despite the significant financial impact, the vulnerability did not directly compromise user funds. Instead, it affected resolver contracts utilizing Fusion v1, which play a crucial role in processing Fusion Swap orders.
In response, 1inch announced that its security team is actively working to mitigate risks and support affected resolvers. The platform urged all resolvers to conduct immediate audits and update their contracts to prevent further incidents.
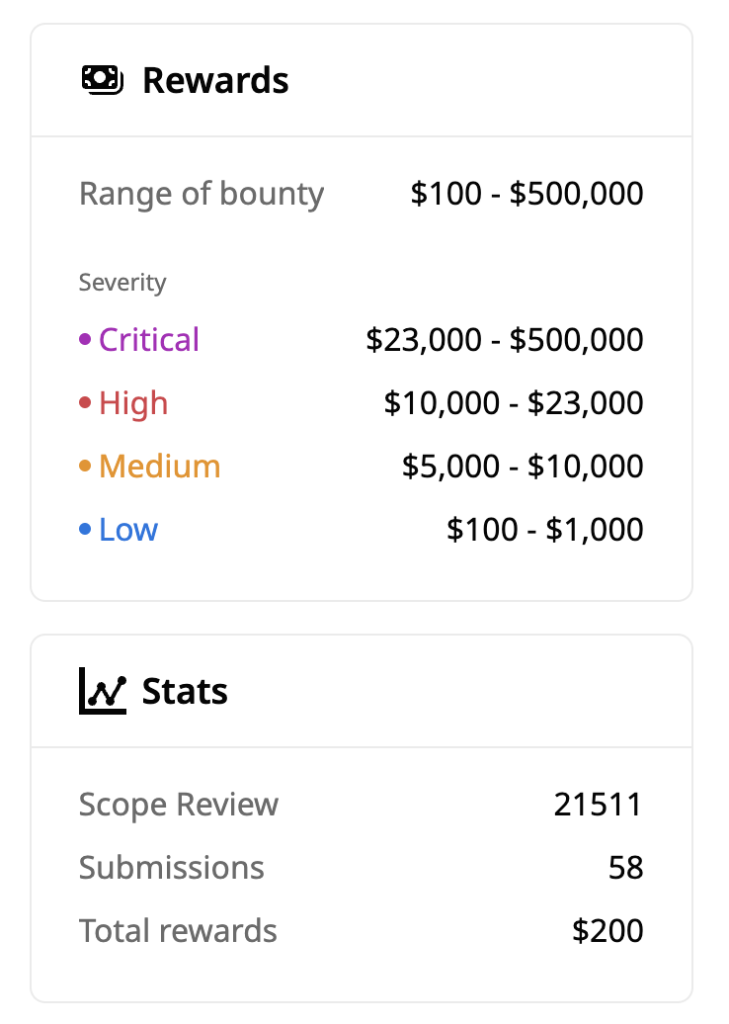
Additionally, 1inch launched a bug bounty program offering rewards ranging from $100 to $500,000 to incentivize security researchers to identify and report vulnerabilities. As of the latest update, the platform has received 58 submissions and paid out $200 in bounties.
Resolvers are integral to 1inch’s ecosystem, acting as automated market makers that assess and fulfill swap orders. Ensuring their security is essential to maintaining the platform’s overall integrity and functionality.
Growing Cybersecurity Threats in the Crypto Industry
The 1inch vulnerability follows a broader trend of security breaches in the crypto industry, including a recent major hack on Bybit.
The centralized exchange reportedly lost over $1.4 billion in an attack linked to the North Korean Lazarus Group. That breach was attributed to a compromised developer’s computer, which allowed attackers to hijack an AWS session token and bypass multi-factor authentication, gaining unauthorized access to Safe Wallet’s infrastructure.
| DISCLAIMER: The information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing. |















![Best Presale Coins To Buy Now: ZKP, Bitcoin Hyper, Remittix, NexChain, & DeepSnitch [Expert Analysis]](https://coincu.com/wp-content/uploads/2026/01/image-51-300x169.jpeg)







