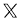$108920.46
At CoinCu News, we give both basic and in-depth articles on the latest news in the cryptocurrency and blockchain sectors.
John Kojo Kumi is a cryptocurrency researcher and writer specializing in emerging startups, tokenomics, and market dynamics within the blockchain ecosystem. With years of experience in crypto journalism and blockchain research, he provides in-depth coverage of decentralized finance (DeFi), NFTs, and Web3 innovations.
He holds a Bachelor of Arts in Geography and Rural Development from Kwame Nkrumah University of Science and Technology, Kumasi, bringing a multidisciplinary perspective to the evolving digital asset space. As a Crypto News Writer, he tracks and reports on industry trends, while his role as a Registrar at the Commission on Human Rights and Administrative Justice reflects his commitment to governance and transparency.
His expertise spans content strategy, SEO optimization, and technical research, enabling him to craft insightful, data-driven analyses. Passionate about blockchain’s transformative potential, he strives to equip readers with the knowledge to navigate the complexities of digital assets and decentralized technologies.
News
David Sacks Discusses U.S. Bitcoin Acquisition Strategy at 2025 Conference
David Sacks, White House crypto czar, explores government's potential Bitcoin acquisition strategy at Bitcoin 2025
May
U.S. Government Explores Potential Bitcoin Acquisitions
White House Crypto Czar David Sacks discusses U.S. government plans for Bitcoin buys, seeking a
May
OKX Plans to Delist 11 Crypto Trading Pairs in 2025
OKX announces the delisting of 11 crypto trading pairs, impacting various investors. Get insights and
May
Brian Quintenz Nominated as CFTC Chair After Crypto Asset Disclosure
Brian Quintenz nominated CFTC Chair, revealing $3.4M in crypto assets. Examines potential impacts.
May
SEC Advances WisdomTree XRP ETF Application to Review
SEC concludes public comments on WisdomTree XRP ETF, further review underway.
May
MetaMask Integrates Solana for Multichain Wallet Accessibility
MetaMask now supports Solana, enabling seamless management of Ethereum and Solana within one interface.
May
BlackRock Ups Bitcoin ETF Holdings by 25%
BlackRock's Bitcoin ETF holdings increased by 25%, highlighting institutional crypto interest.
May
Worldcoin Sells $135 Million in Tokens, Enhancing U.S. Expansion
Worldcoin boosts U.S. presence with $135 million token sale, driving tech growth.
May
Nasdaq Submits 21Shares SUI ETF Form to SEC
Nasdaq submits form for 21Shares SUI ETF to SEC for approval.
May
[tptn_list how_old="7" limit="5" title_length="0" heading="0" show_date="0" ]
[tptn_list how_old="30" limit="5" title_length="0" heading="0" show_date="0" ]