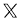$107908.728
At CoinCu News, we give both basic and in-depth articles on the latest news in the cryptocurrency and blockchain sectors.
John Kojo Kumi is a cryptocurrency researcher and writer specializing in emerging startups, tokenomics, and market dynamics within the blockchain ecosystem. With years of experience in crypto journalism and blockchain research, he provides in-depth coverage of decentralized finance (DeFi), NFTs, and Web3 innovations.
He holds a Bachelor of Arts in Geography and Rural Development from Kwame Nkrumah University of Science and Technology, Kumasi, bringing a multidisciplinary perspective to the evolving digital asset space. As a Crypto News Writer, he tracks and reports on industry trends, while his role as a Registrar at the Commission on Human Rights and Administrative Justice reflects his commitment to governance and transparency.
His expertise spans content strategy, SEO optimization, and technical research, enabling him to craft insightful, data-driven analyses. Passionate about blockchain’s transformative potential, he strives to equip readers with the knowledge to navigate the complexities of digital assets and decentralized technologies.
News
ChainCatcher Hosts “Midfield Battle of BN Alpha” Space Event
ChainCatcher holds BN Alpha Space event. Industry veterans discuss subsidy impacts, growth potential.
May
U.S. Court Halts Trump’s Liberation Day Tariffs
U.S. Court blocks Trump's Liberation Day tariffs, affecting small businesses and trade regulations.
May
U.S. Vice President Allegedly Supports Cryptocurrency as Inflation Hedge
U.S. Vice President Vance allegedly endorses Bitcoin as a hedge against inflation, stirring market speculation.
May
BlackRock Eyes 10% Stake in Circle’s IPO: Bloomberg
BlackRock plans to acquire 10% of Circle's IPO shares, spotlighting institutional interest in USDC's stablecoin
May
US Banks Explore Cryptocurrency Amid Regulatory Shift
Key US banks cautiously expand crypto operations, exploring stablecoins and custody services amid regulatory changes.
May
U.S. VP Vance Discusses GENIUS Act at Bitcoin Conference
U.S. VP J.D. Vance addresses Bitcoin 2025, discussing GENIUS Act's stablecoin impacts.
May
US Vice President’s Crypto Stance Lacks Verification Amid Bitcoin 2025
No verified statement from the US Vice President at Bitcoin 2025 on crypto regulation rollback,
May
SEC Hosts DeFi Roundtable on Future Regulatory Approaches
SEC's June 9 DeFi roundtable signals a shift towards collaborative crypto regulation, engaging key financial
May
SOL Strategies Aims to Raise $1 Billion via Prospectus Filing
Canadian firm SOL Strategies files for up to $1 billion funding to expand Solana investments.
May
[tptn_list how_old="7" limit="5" title_length="0" heading="0" show_date="0" ]
[tptn_list how_old="30" limit="5" title_length="0" heading="0" show_date="0" ]